CYBER SECURITY
Things?
Cyber security is the set of technologies, processes and measures to protect the operation of information systems and the company's information assets (data) from threats of all kinds.
An adequate protection and safety management system guarantees:
- integrity, confidentiality, availability
of data, information and IT services.
THE MAIN THREATS

- Ransomware attacks: attacks in which cyber criminals take control of the victim's assets which they will only make available for a ransom.DDoS threats: attacks that prevent users of a network or system from accessing information, services and other resourcesMalware: malicious software designed to damage a device, alter its operation, or gain unauthorized access. Social engineering and phishing threats: threats that attempt to exploit human error or human behavior to access information or services. Data threats: attacks aimed at obtain unauthorized access to data or manipulate data to interfere with system behavior.
- Internet Threats: Attacks that affect the availability of the Internet. For example the so-called BGP (Border Gateway Protocol) hijacking or BGP hijacKing.Disinformation - bad information: intentional attack that consists in creating or sharing false or misleading information to manipulate public opinion.Attacks on supply chains: strategy with which it is attacked an organization by hitting the weak points of its IT supply chain (and not only!) with potential cascading repercussions. Cyberwar: attacks by hostile nations, criminal organizations or terrorists against the infrastructures and institutions of a state, to cause serious damage and loss of life.
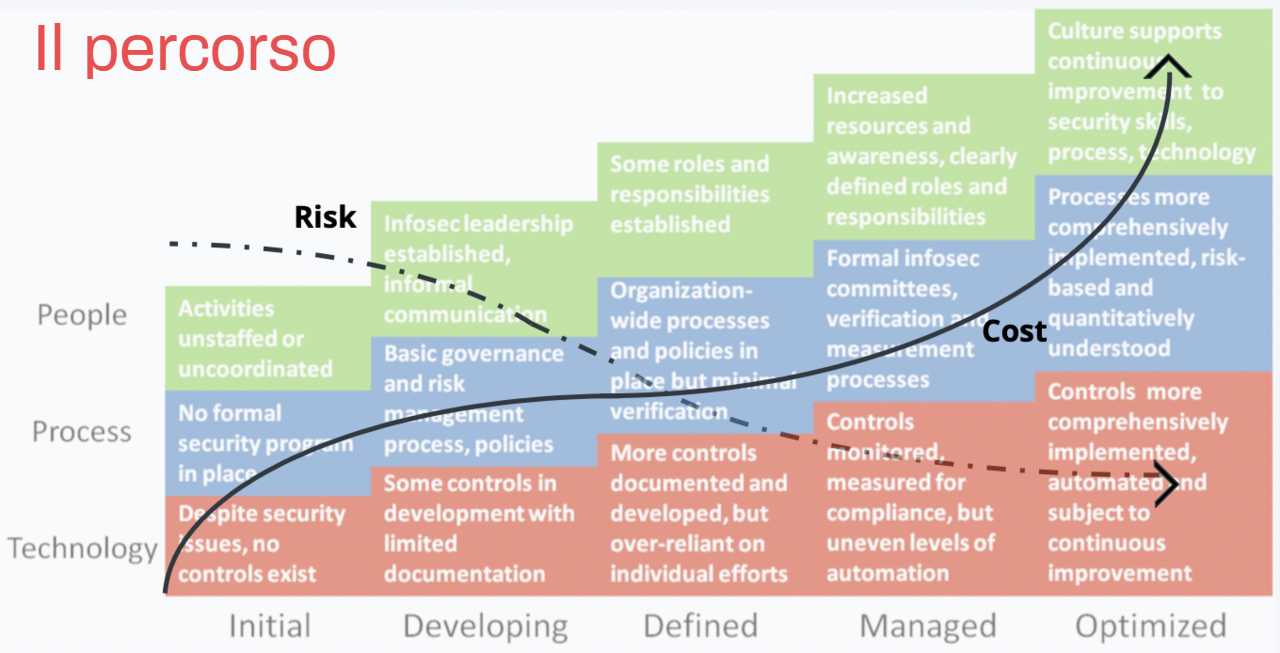
The phases of the journey
The benefits

- Optimization of RTO and RPO (the main parameters for data recovery) Guarantee of operational continuity of systems Reduction of costs caused by interruptions (downtime) Protection of the company's reputation Control and optimization of the performance of your Disaster Recovery solution
- Definition of clear and effective actions to deal with an unexpected situation and guide the restoration of operations Granular management of necessary interventions Minimization of impacts on the performance of information systems






